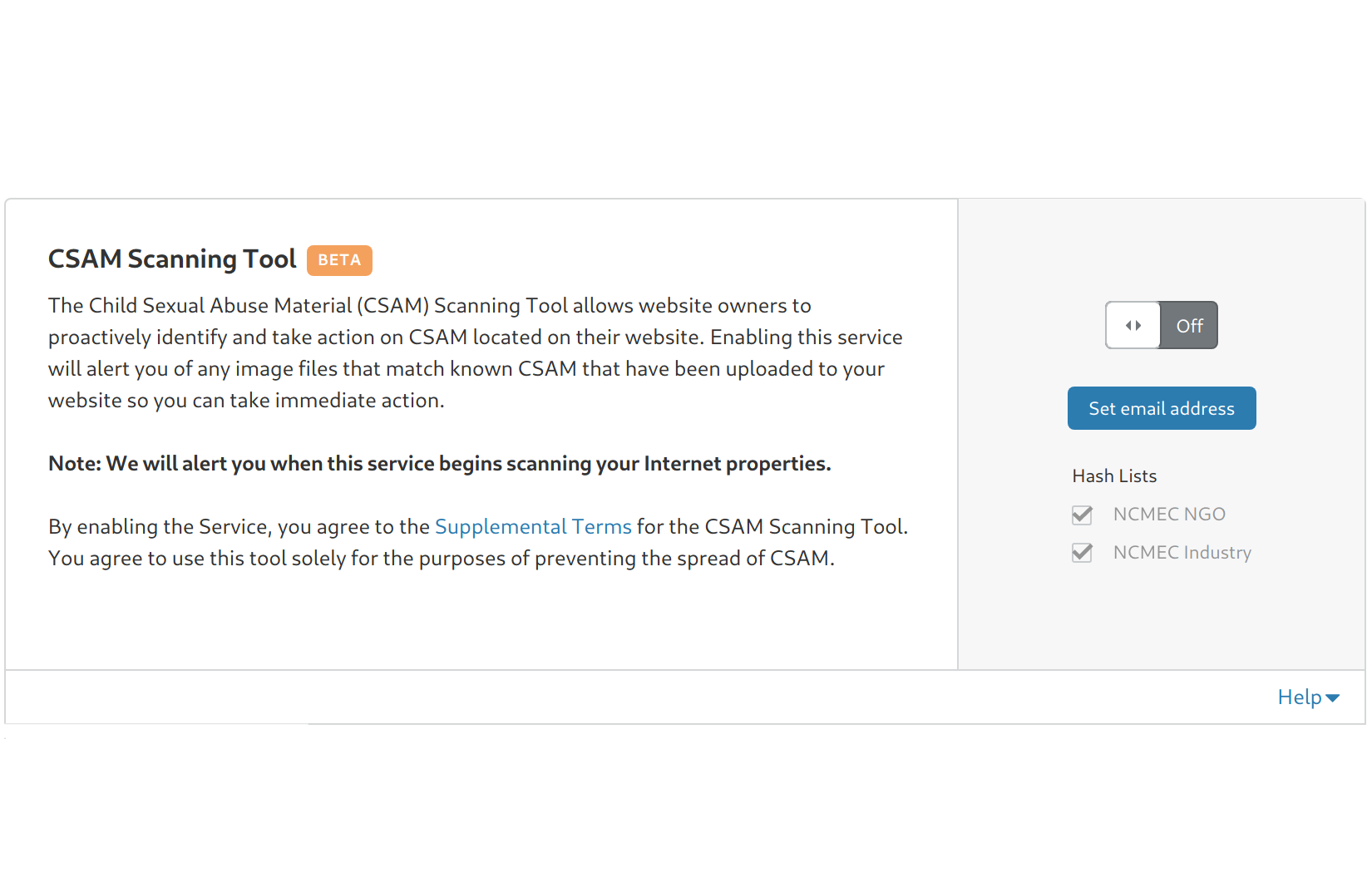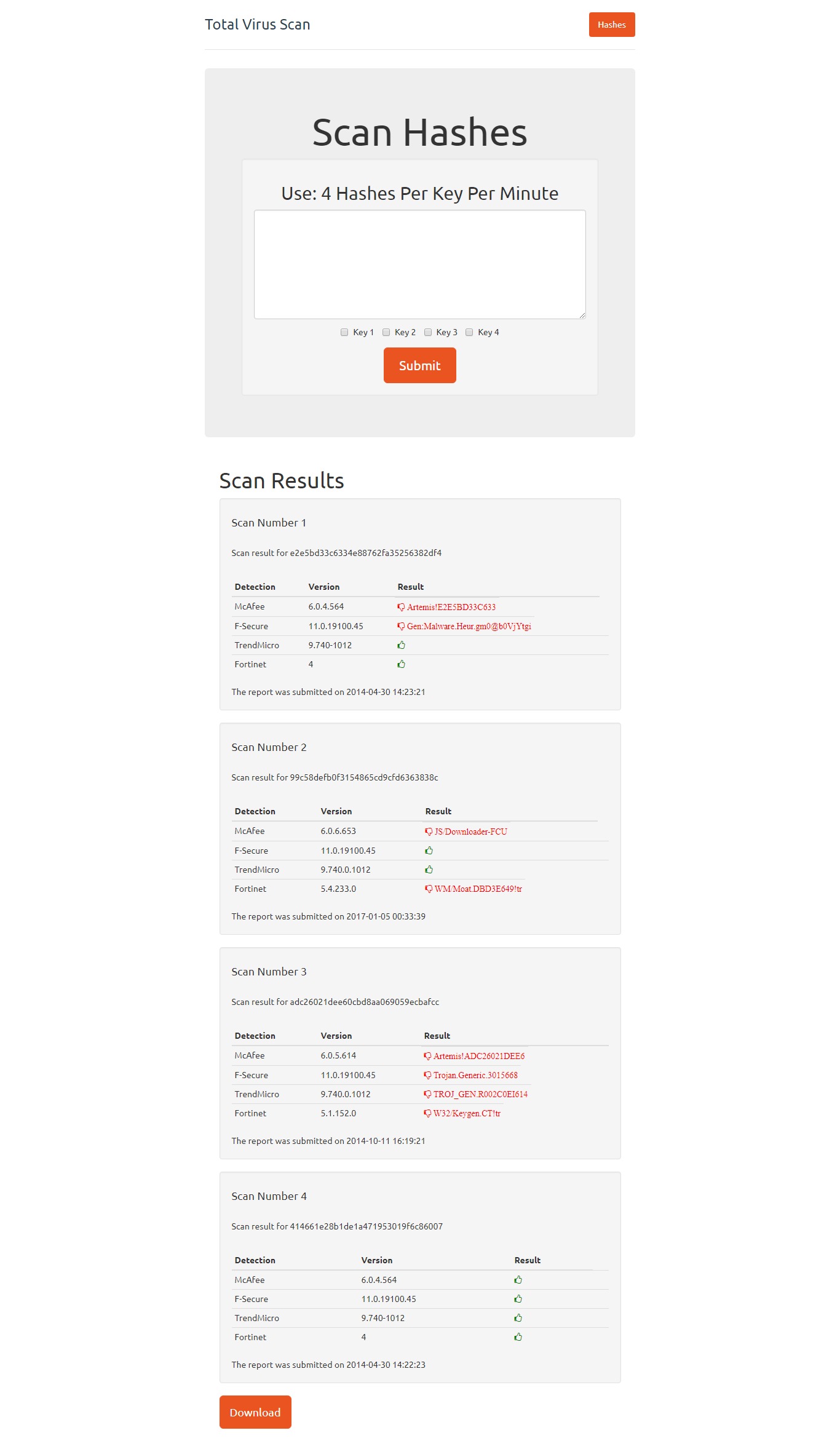
GitHub - sceptreone/Virus-Total-Mass-Hash-Scanner: Single Page site which helps scanning multiple hashes using limited API keys from VirusTotal.
GitHub - sceptreone/Virus-Total-Mass-Hash-Scanner: Single Page site which helps scanning multiple hashes using limited API keys from VirusTotal.

Angel Toner - Xerox AltaLink B8045 Multi-Function Mono Laser Printer Scanner Copier All in One, Tabloid-size https://www.ebay.com/itm/Xerox-AltaLink-B8045-Tabloid-Multi-Function-Mono-Printer- Scanner-Copier-45PPM-A3/153078765142?hash=item23a4349656:g ...






![PDF] Hash-AV: fast virus signature scanning by cache-resident filters | Semantic Scholar PDF] Hash-AV: fast virus signature scanning by cache-resident filters | Semantic Scholar](https://d3i71xaburhd42.cloudfront.net/300696698acf5a3e39bc21897cca02272effeb73/4-Table1-1.png)